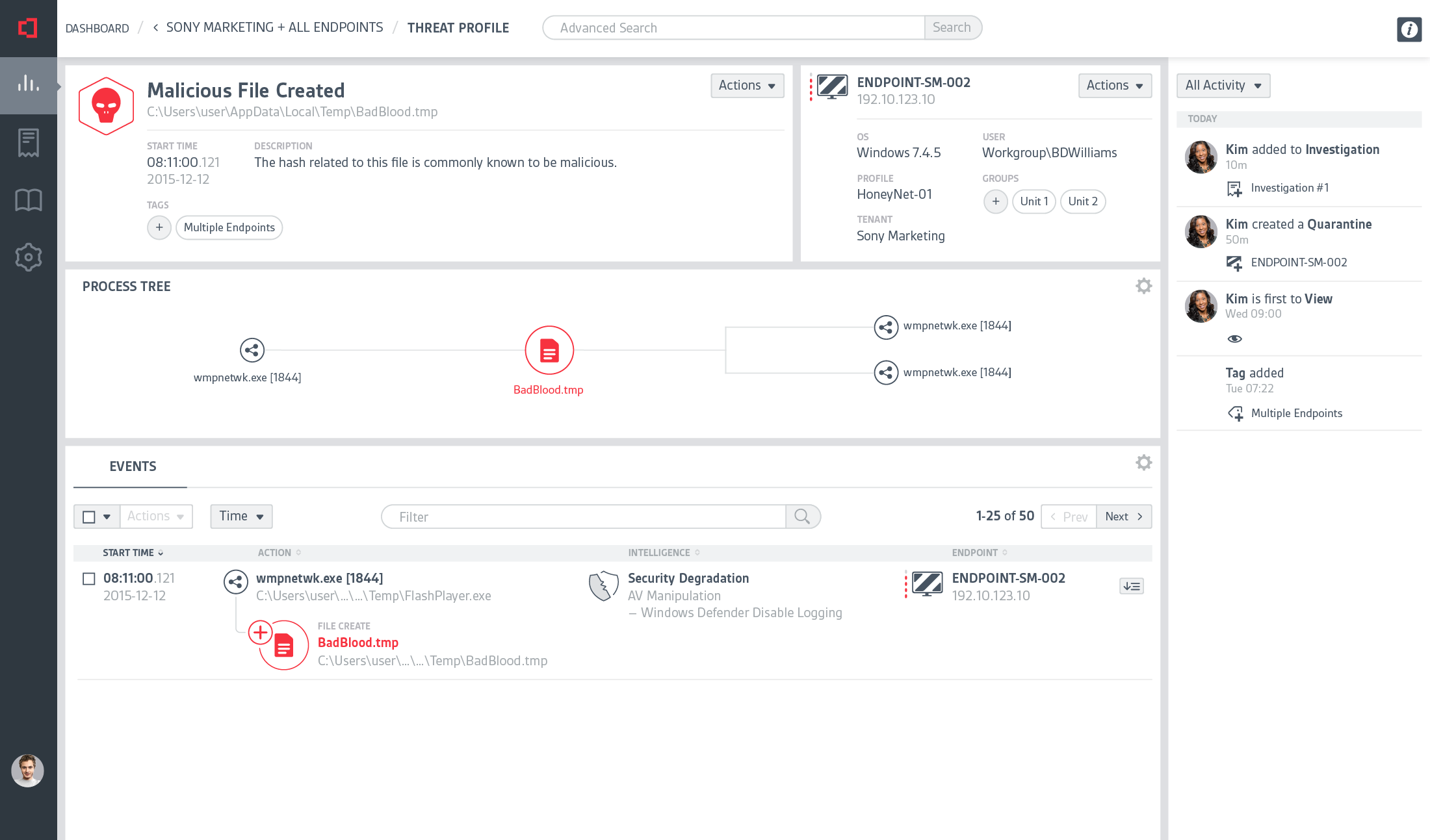
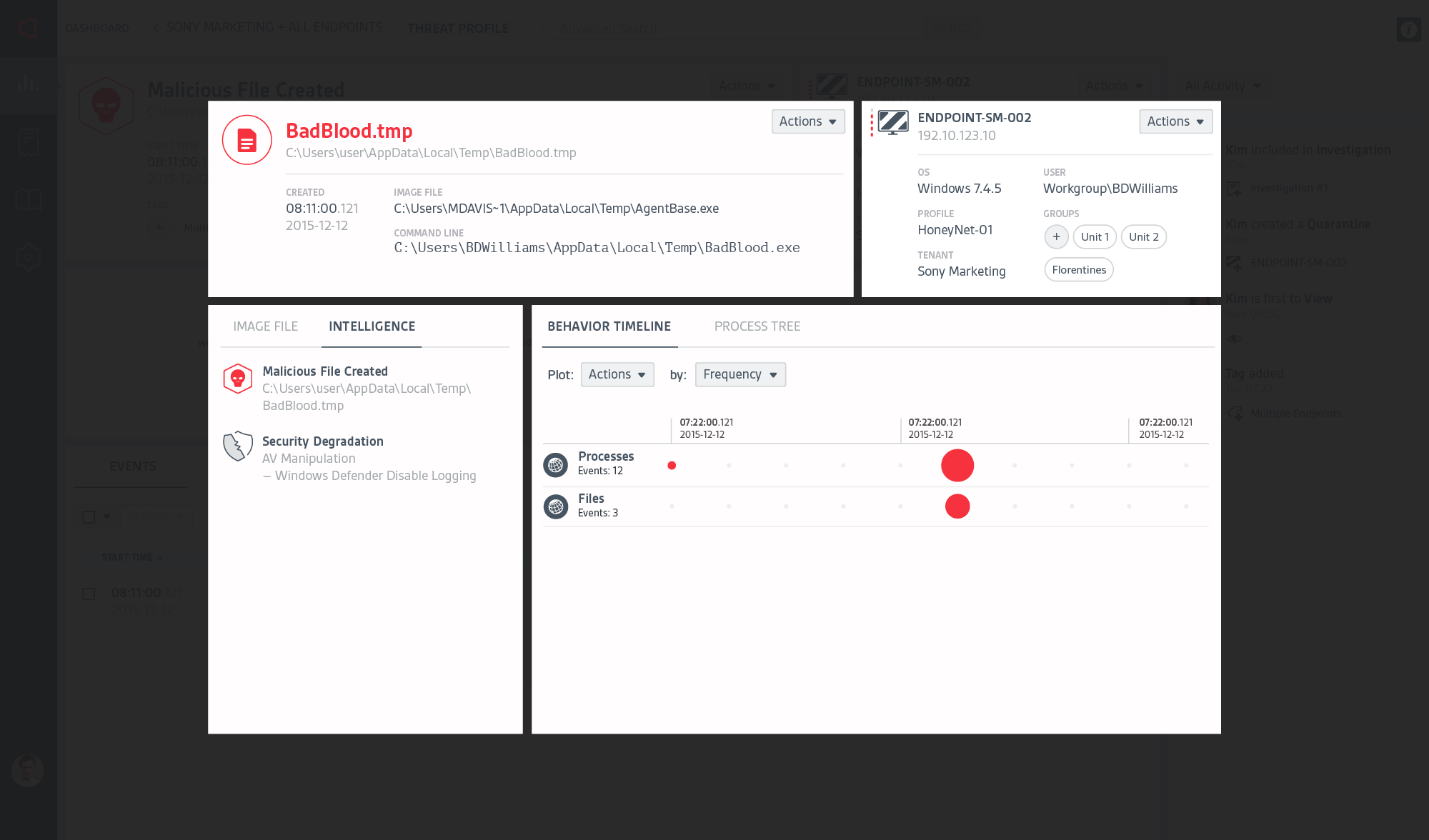
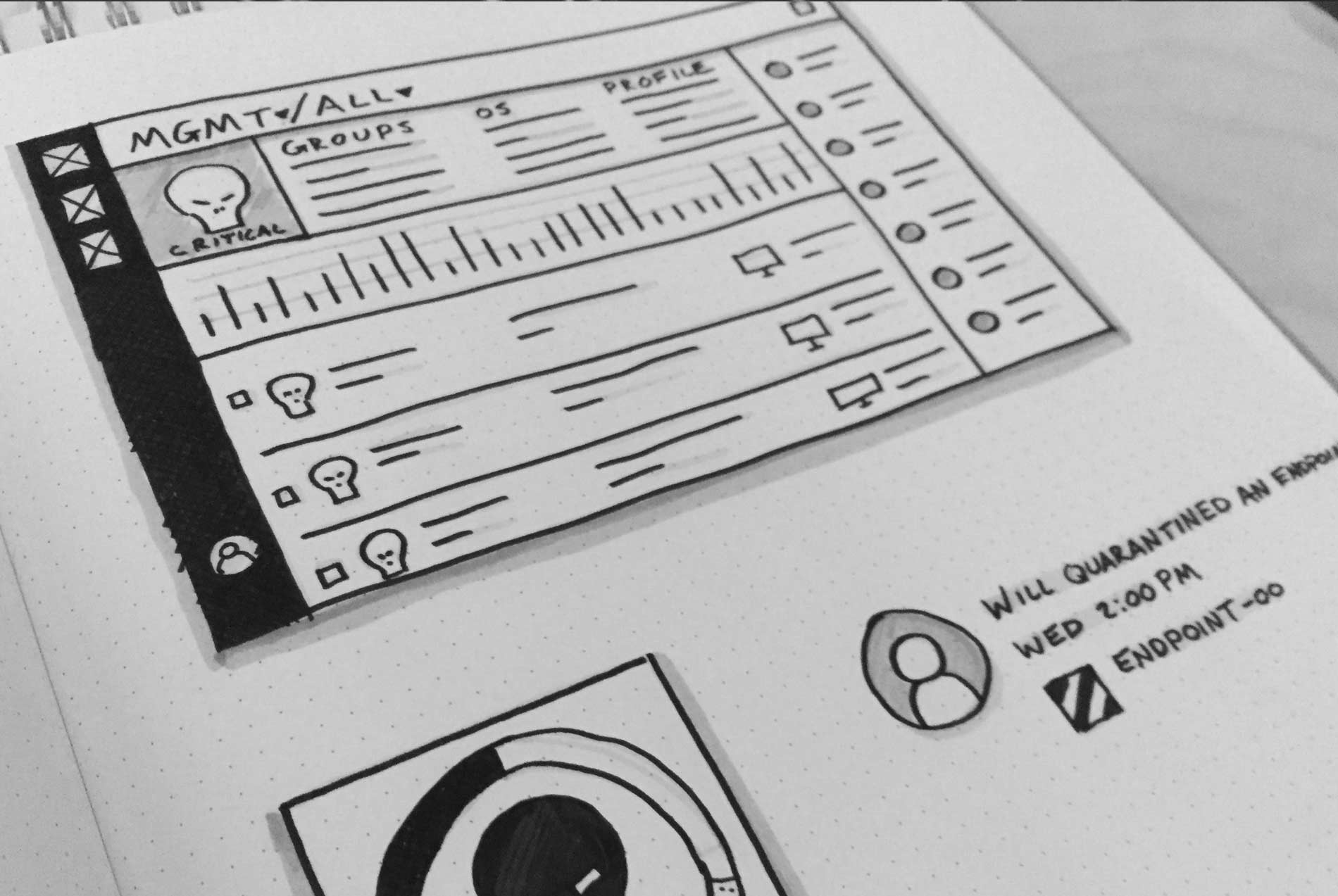
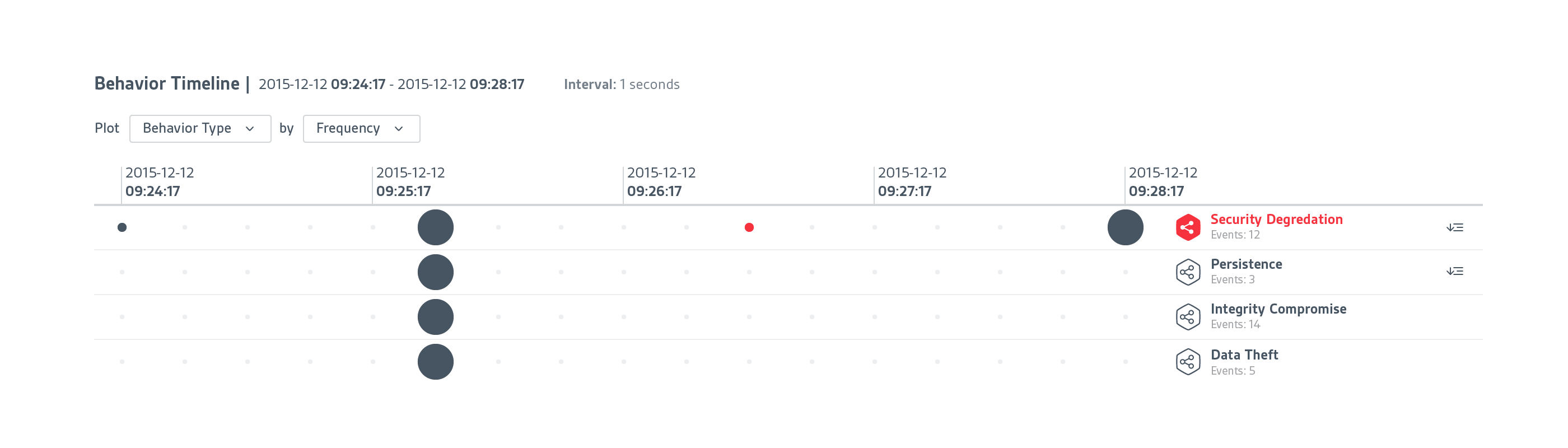
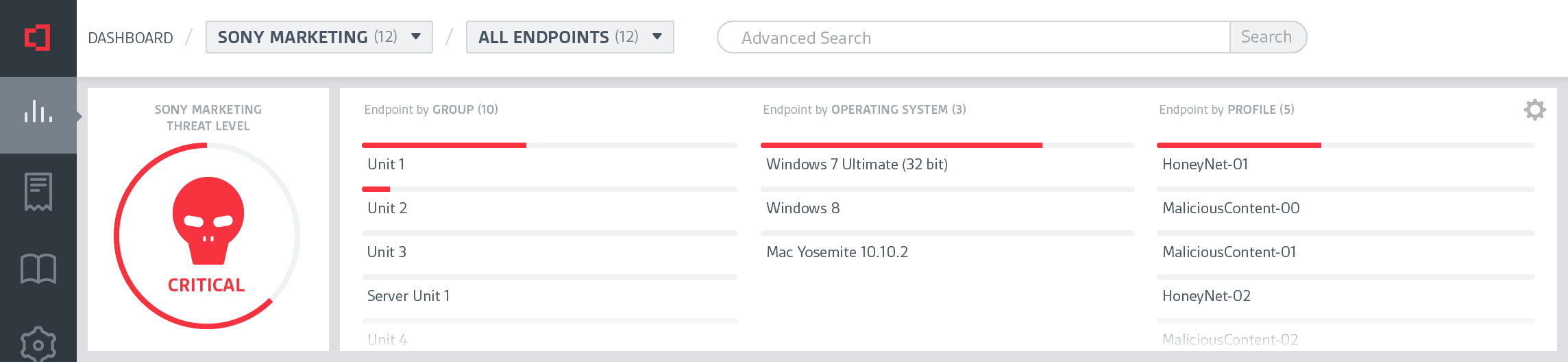
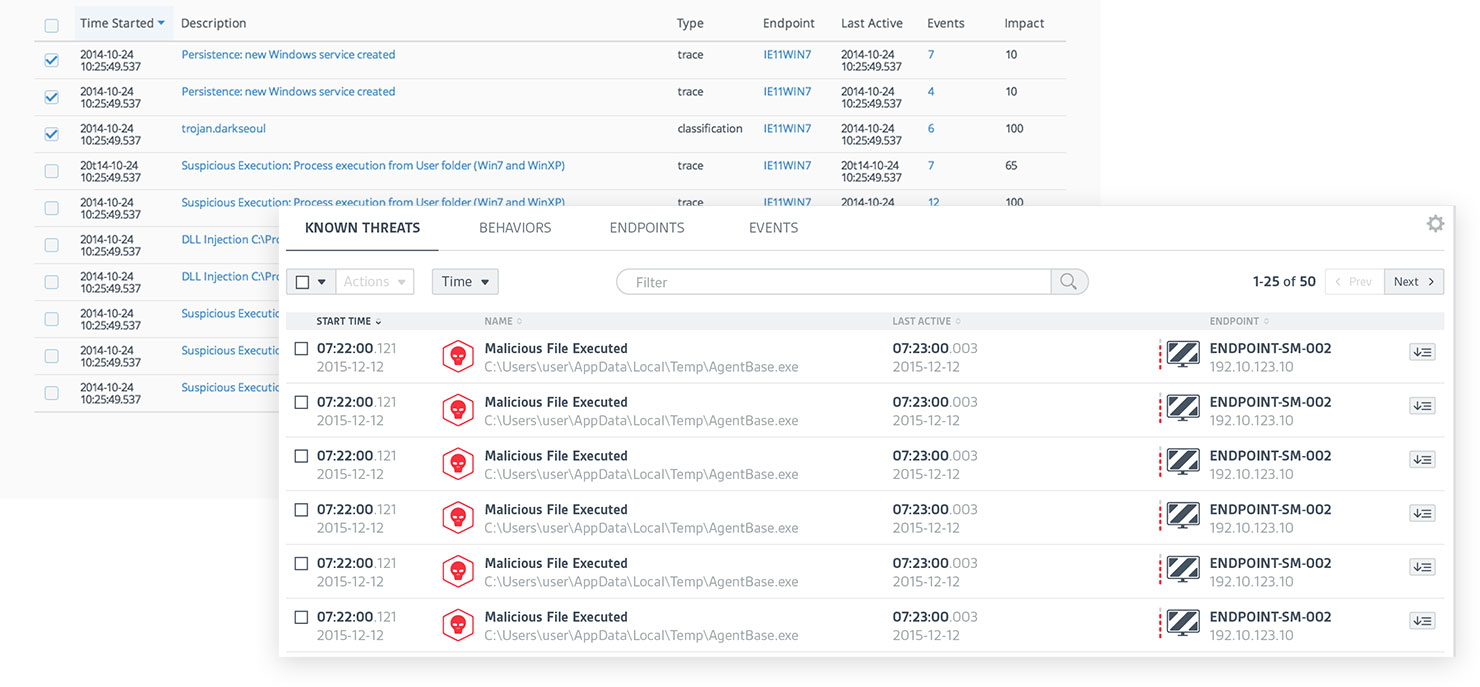
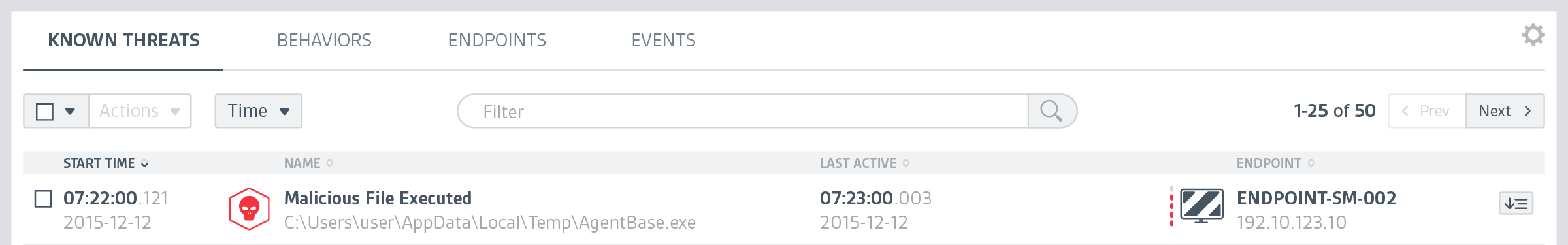
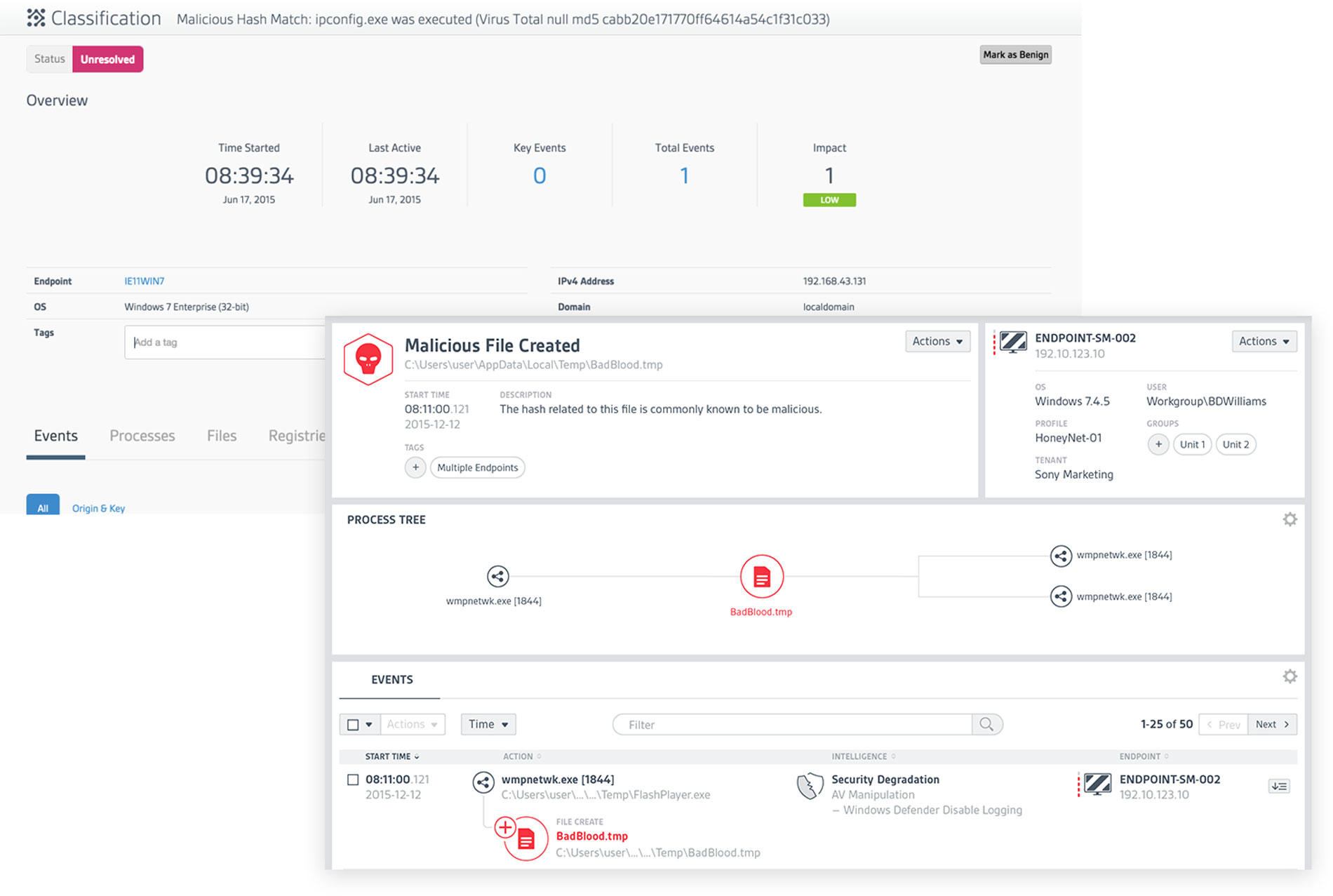
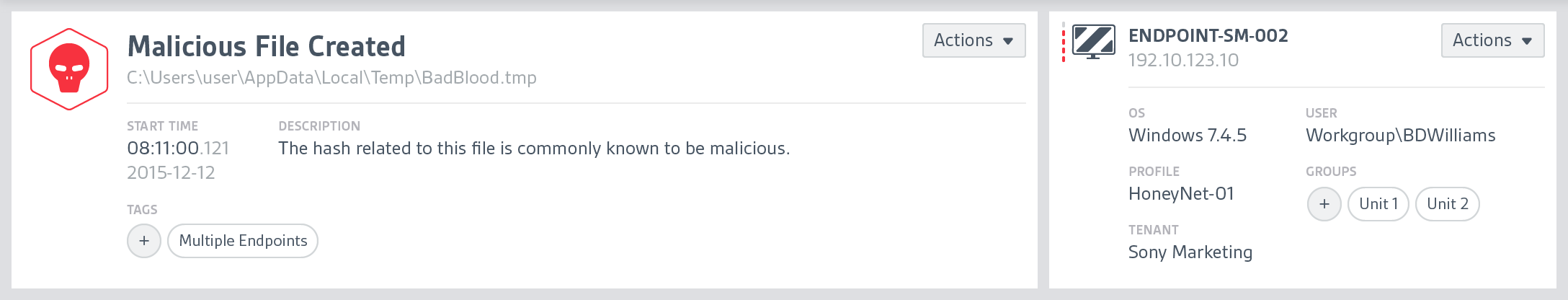
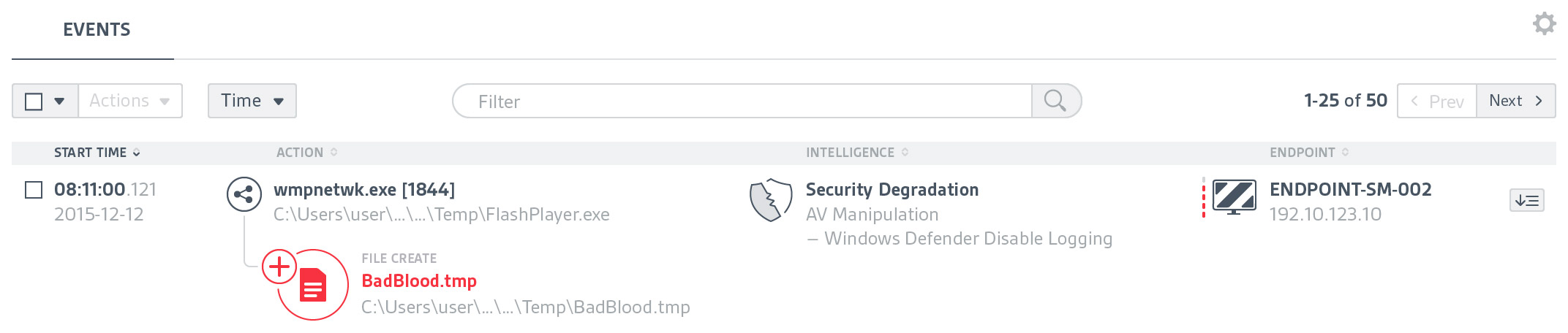
At CounterTack, our product was very useful for finding specific data that a user already knew something about, but it was a struggle for them to browse the data. There was just too much navigational friction, loose information architecture, and lack of visual clues to give users a clear path.
It was my responsibility to not only help clarify the user's journey through the product, but to clean up the interface so users can quickly find what they need.