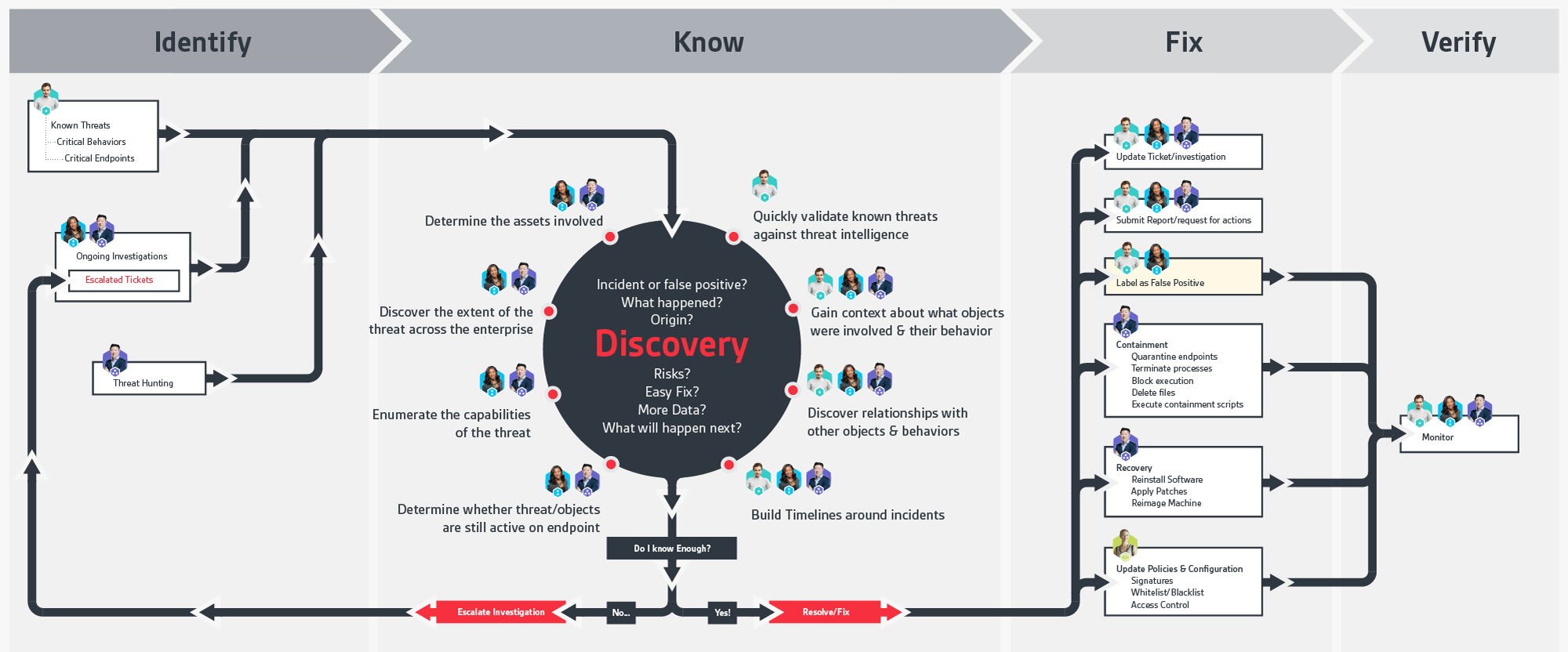
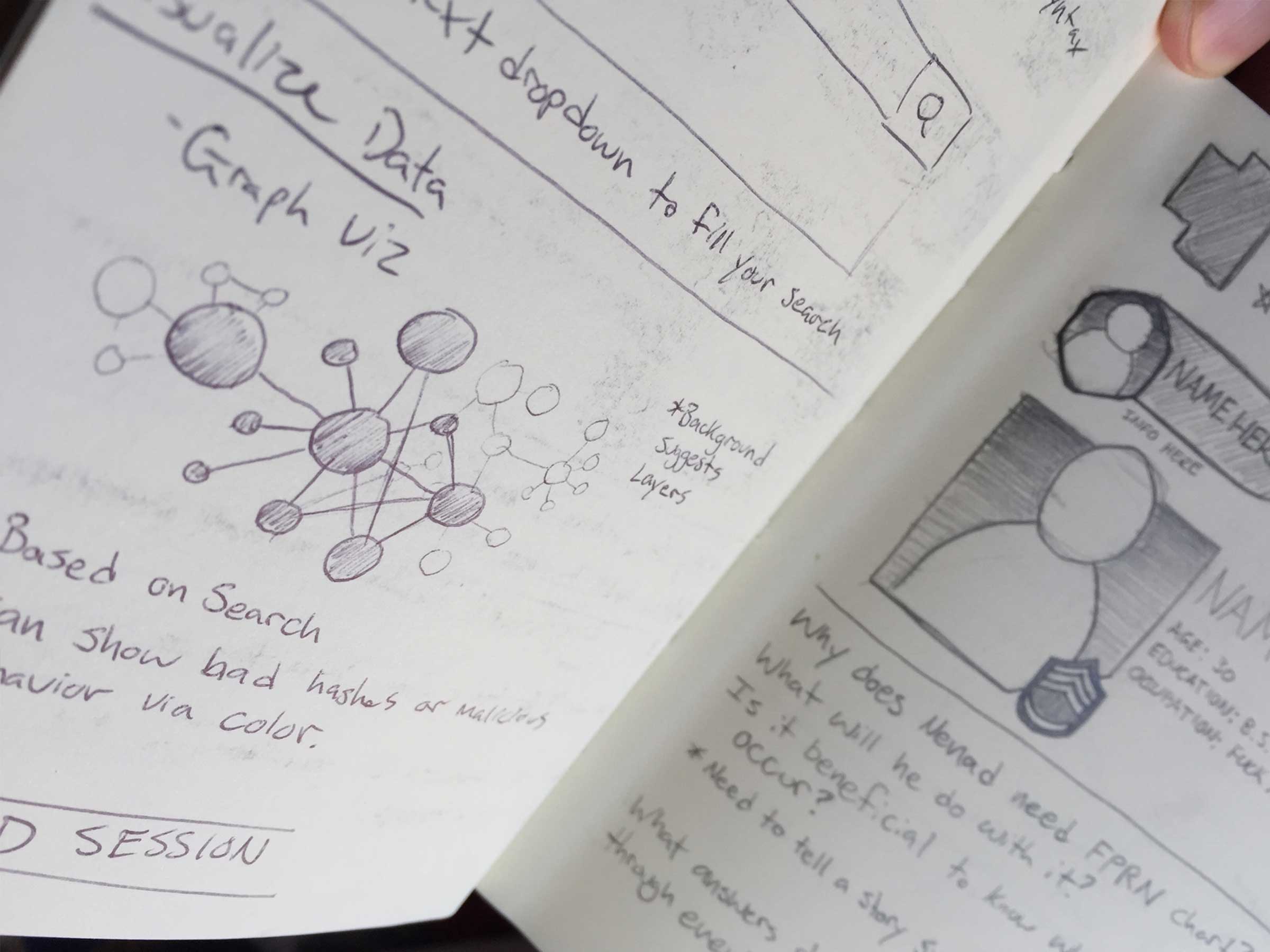
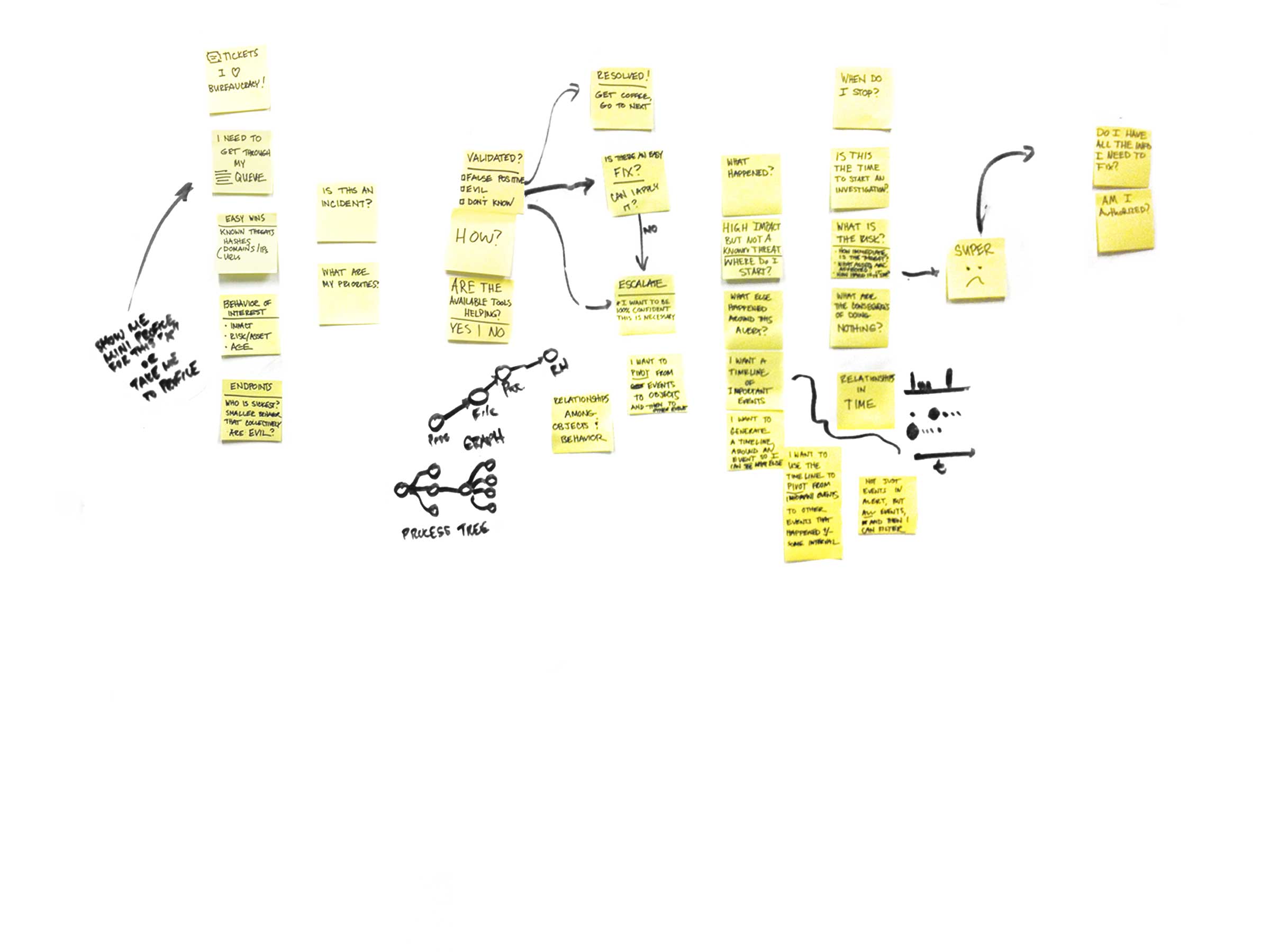
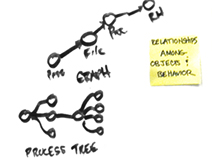
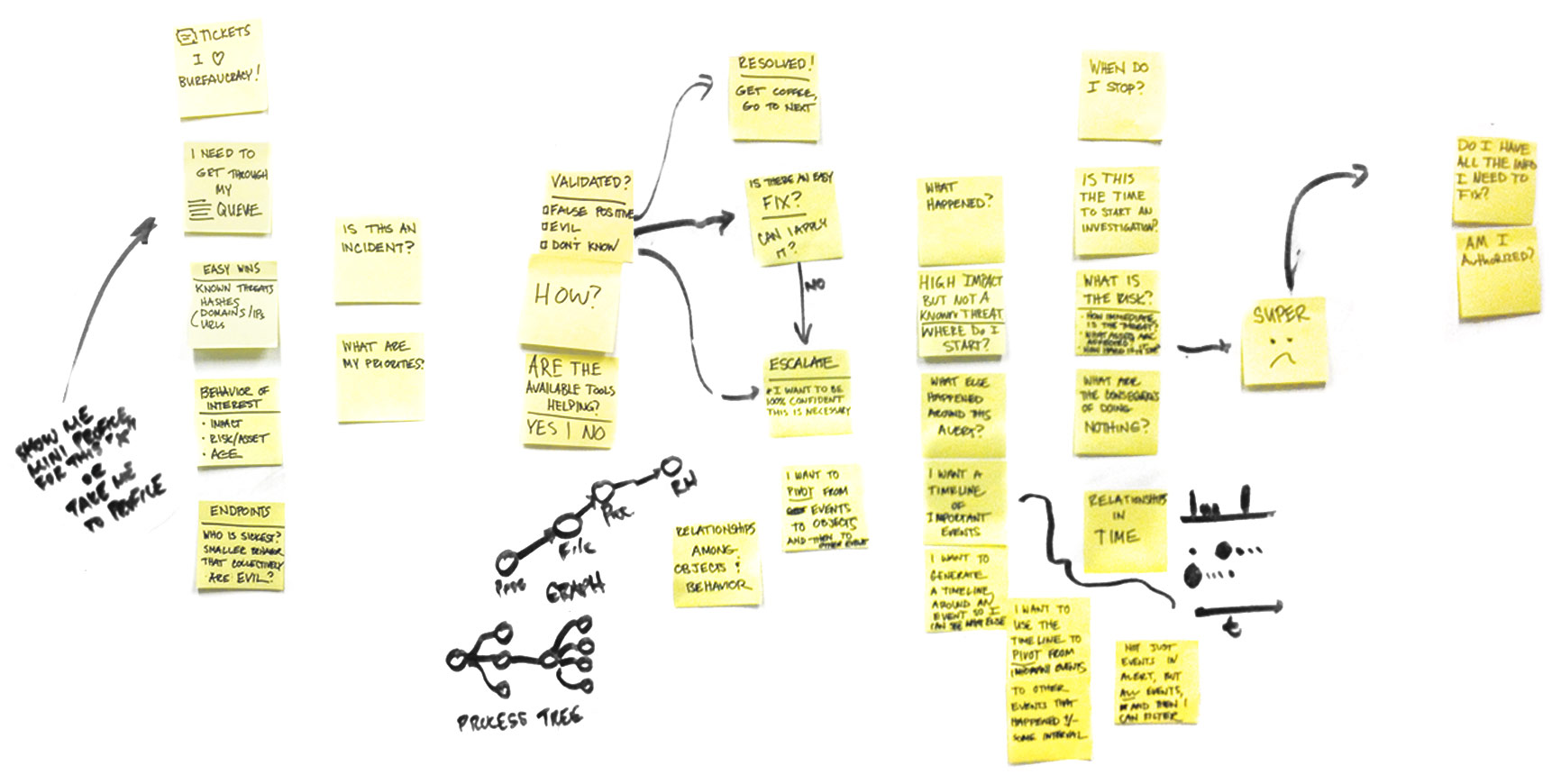
We had to go back to the drawing board to figure out how exactly our users could make full use of our product.
The technology was great, but we didn't really know how the product was being used, and we needed to step waaay back to get a look at not only what our users goals and pain points were, but who they were as well.